Insider Threat Protection: How DDR Can Help
In 2023, Tesla suffered an enormous information breach that affected 75,000 workers whose information, together with names, cellphone numbers, and Social Security Numbers had been leaked. According to the media outfit to which the information was leaked, even billionaire CEO Elon Musk‘s Social Security quantity was included within the over 100 gigabytes of leaked information.
Investigations recognized two former workers as accountable for the leak, which is neither the primary of its variety hitting a serious international firm, nor will or not it’s the final, not less than if latest developments on insider threats are to be taken significantly. And they completely ought to.
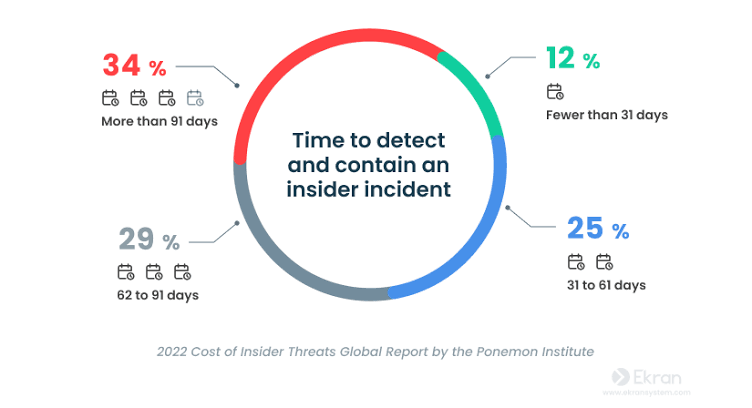
Only 12% of insider incidents are detected and contained throughout the first month of their prevalence, and this is the reason organizations want to change to sensible real-time monitoring options such because the rising information detection and response (DDR) strategy.
Briefly: The State of Insider Threat
According to a report by Securonix, 76% of organizations reported insider assaults as towards 66% in 2019. Yet, solely 16% contemplate themselves ready sufficient to deal with such threats.
If the present instruments and packages that firms use are proving ineffective towards insider threats, then what hope do enterprises have in combatting this perennial problem? In a 12 months, nearly all of organizations will expertise between 21 and 40 insider assaults, every endangering the very existence of firms attacked.
Understanding the Nature of Insider Threats
Time after time, one finds that malicious insiders who launch assaults based mostly on the privilege they’ve are pushed by greed or some form of ideology, not hesitating to steal delicate information, mental property, and commerce secrets and techniques for private acquire.
But some would possibly simply be pushed by disgruntlement, particularly for individuals who work in a poisonous work surroundings, as analysis exhibits. A destructive office tradition can simply erode an worker’s sense of loyalty and dedication to the group.
Therefore, even when they aren’t straight committing the acts themselves, sad workers might really feel much less inclined to guard the corporate’s pursuits and could also be extra prone to interact in dangerous or unethical behaviour that compromises safety.
That or they could merely change into negligent, as happens in 55% of insider threats, and that is one thing that happens even when the office tradition is favorable. The hybrid/distant work tradition does not assist both.
In addition, workers who work in a constructive tradition and are usually not correctly educated on safety protocols, insurance policies, and finest practices are very prone to inadvertently expose delicate info or create or permit vulnerabilities that malicious attackers can exploit.
What’s the Solution?
All these are to not say that one can repair insider threats by establishing a constructive tradition and instituting safety coaching. Sometimes, insider threats can come up because of a failure of coverage, such because the offboarding course of. Such a failure should have been the reason for Tesla’s woes.
Even non-malicious former workers, by being allowed to retain firm information can show harmful. And that is with out but contemplating third-party distributors, companions, contract workers, and so forth. Many of those entities might acquire entry to some form of information to do their jobs for a short time, after which they dwell completely with them.
The most important problem with coping with insider threats is that many people do not contemplate their multifaceted nature. There ought to be a essential emphasis and concentrate on the plurality and multifaceted nature of assaults launched or allowed by insiders.
A single risk by a lone insider can, on the similar time, expose the group to ransomware, information privateness points, regulatory sanctions, company espionage, and naturally, vital cash loss. This cascading impression can successfully be the tip of any firm, no matter its previous resilience.
As such, the precise answer to insider assaults have to be one which inherently acknowledges the dynamic nature of this type of risk.
Enter Data Detection and Response
In the cybersecurity trade, it seems that nearly each month, a brand new answer or acronym is launched with the promise of fixing all the issues that had been beforehand unsolvable. Therefore, many firms have ended up with a mounting assortment of a number of cybersecurity instruments that do not appear to have achieved a lot. These embody DLP, LAM, behavioural analytics, endpoint detection, and so forth.
But what if what wants to vary is the strategy to information safety?
For one, information is commonly labeled for significance and sensitivity based mostly purely on the content material. This is just not fully fallacious, however anybody who works with information will let you know that it is not simply the content material on a desk or information body that issues; the context does too, making the next sorts of questions, and much more, essential:
- Who has accessed the information?
- Who can entry the information?
- How has the information modified just lately?
- Where has the information been used?
- When was the information accessed?
- How was the information accessed?
These are questions that time to the lineage of the info, an essential think about figuring out easy methods to deal with information. Why is that this so essential? Data is most weak when it’s in transit. There are super-safe methods to deal with information at relaxation and information in use. Yet, securing information in movement is a big problem.
And that’s what Data Detection and Response solves, by making use of real-time monitoring not simply to the gadgets (endpoints) by means of which the information is accessed or to the individuals who entry the information, however to the information itself.
The primary thought of DDR is to comply with the information wherever it goes, and when the information is about for use or accessed inappropriately, the system well intervenes. In this fashion, even insiders are usually not free to work together with information in unauthorized methods.
Conclusion
Today’s workplaces are dynamic and the strategy to cybersecurity additionally must be dynamic with a purpose to stay on prime of threats and vulnerabilities. By deploying real-time monitoring, DDR permits cybersecurity groups to catch breaches proper earlier than they even happen and defend any form of compromised information.
The submit Insider Threat Protection: How DDR Can Help appeared first on Datafloq.