Most Common Causes of Data Leakage in 2023
Given the worth positioned on information in this age, breaching methods to trigger information leaks is unsurprisingly the mainstay of malicious cyber actors right this moment. And companies are nonetheless grappling with this actuality and leaving their defenses open regardless of the spate of rising information leakages and breaches globally.
Understanding the widespread causes of information leaks is essential for implementing efficient cybersecurity measures. In this text, we discover 5 of the outstanding causes, highlighting how they happen in addition to examples to show the pervasiveness of information leaks.
Software Misconfiguration
Despite the obvious hazard, many people and organizations depart default passwords unchanged. This is only one instance of how misconfiguration of settings can permit attackers to infiltrate methods, databases, cloud providers, functions, and so forth. At different occasions, a misconfiguration can happen when a program’s settings don’t align with the group’s safety coverage, and so permits unintended habits.
This is primary cyber hygiene, however even massive tech corporations can depart sure issues out. Back in 2021, for instance, Microsoft made the information for the unsuitable causes when 38 million buyer information together with delicate info had been uncovered on-line as a result of a misconfiguration of its Power Apps portal service.
Particularly, organizations must be cautious when migrating providers or information to cloud environments – misconfigurations are widespread with this motion and might come up merely from not following or not understanding the directions.
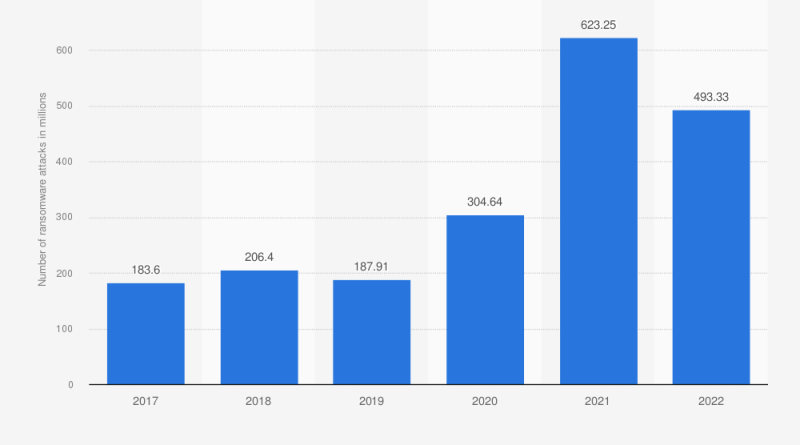
Ransomware
According to a latest report on the state of ransomware, international ransomware assaults surged in the previous yr and recorded an all-time eye. Amidst these, the US is the largest sufferer, struggling 43% of international recorded assaults, with zero-day exploitations by malicious actors taking part in an enormous function in the rise in assaults.
So, ransomware assaults are usually not solely rising in quantity but in addition in sophistication. And for this, organizations need to heighten their vigilance to forestall information leaks.
Source: Statista
Notably, DISH, the satellite tv for pc broadcast firm was hit by a ransomware assault in February. The assault led to vital outages in its inner servers and IT methods and leaked private info belonging to about 300,000 individuals. But this is just one of the a number of ransomware assaults which have hit numerous organizations and services.
Data Theft
Over the previous few years, insider assaults have change into a rising concern, with malicious insiders changing into significantly a fear for information theft. Such considerations contributed to the event of zero-trust cybersecurity options since anybody generally is a malicious insider, with better dangers assigned to privileged customers with entry to delicate info.
Source: Statista
This is to not rule out the function of exterior components in information theft, although. A German newspaper, earlier this yr, ran a report detailing a myriad of security considerations expressed by Tesla clients. According to the electrical automotive firm, the confidential information offered to the newspaper was stolen from its system, though it could not inform whether or not an insider was accountable or an exterior actor.
Third-Party Breach
Third-party breaches have change into a very helpful mode of assault for malicious actors as a result of of the potential of buying a number of victims from only one hit. For occasion, in keeping with a third-party breach report, in 2022, 63 vendor assaults led to 298 information breaches throughout corporations.
In January, two insurance coverage corporations – Aflac and Zurich Auto Insurance – suffered a information leak that affected tens of millions of information together with the data of no less than 2 million policyholders with the 2 corporations mixed. According to stories, an unnamed US subcontractor was concerned though it was not sure that each information breaches had been related.
This exhibits the cascading results of third-party information breaches and underscores why organizations should cease at nothing to make sure that they solely accomplice with corporations and distributors which have sturdy safety protocols in place.
Software (API) Vulnerability
APIs had been a groundbreaking revelation in software program growth, however their proliferation has exacerbated the dangers of information publicity since delicate information is more and more being shared through this medium. So, API vulnerabilities, comparable to damaged authentication points simply jeopardize the software program’s safety and might permit malicious actors to entry information illegally.
Source: VentureBeat
An API vulnerability in Twitter’s software program allowed menace actors to steal the e-mail information of over 200 million customers. Although this occurred again in 2021 and the breach was mounted in January the next yr, by mid-2022, the information units began occurring sale on the darkish net and had been ultimately printed without cost. Email information are typical targets for phishing and social engineering assaults.
How to Prevent Data Leakage
Preventing information leakage will not be an not possible job, though, as a result of more and more subtle nature of cyber assaults today, it may be very powerful to deal with. However, these few steps ought to assist you to overcome the most typical causes of information leakage.
- Implement a robust information detection and response answer: Unlike conventional information loss prevention methods, DDR options prioritize behavioral analytics and real-time monitoring through machine studying to robotically establish and reply to information incidents.
- Evaluate third-party dangers: working with a 3rd get together, particularly when it entails exchanging information, can not be enterprise as ordinary. The dangers of your companions are yours too, so you will need to know the place each corporations stand and how one can complement, not endanger, one another, security-wise.
- Secure all endpoints: there was an enormous improve in the quantity of distant entry factors that talk with enterprise networks. Plus, they’re dispersed too, and typically internationally. Adopting a zero-trust strategy helps forestall endpoints from changing into leeway for assaults.
- Cybersecurity hygiene: as recognized earlier, information leakage can merely be as a result of unhygienic practices. Methods comparable to encryption, information backups, password administration, and so forth. are usually not outdated; they need to all be in place that will help you keep your guard.
Conclusion
Proactive measures, common safety assessments, and a complete cybersecurity technique are key to mitigating the dangers related to information leakage. As we’ve seen from the examples, all kinds of enterprise, even the largest tech corporations, suffers from this problem. Therefore, information safety is one thing that each one enterprise leaders should take critically from now.
The publish Most Common Causes of Data Leakage in 2023 appeared first on Datafloq.