IIoT Security Challenges & Tips to Navigate Them
Back in 2010, a nuclear plant in Natanz, Iran, fell sufferer to the Stuxnet malware that focused Simatic Step 7, a software program product for configuring and working programmable logic controllers (PLCs). The assault allowed hackers to exploit the PLC models throughout the manufacturing unit and harm nearly one thousand uranium enrichment centrifuges, delivering a extreme blow to the nation’s nuclear program.
In the case of Iran, this was not essentially a foul factor; we do not actually need extra nuclear weapons round, will we?
But think about it was your manufacturing unit, your tools value a number of million {dollars} apiece, and your status at stake.
It’s at all times helpful to put issues into perspective, proper?
What we’re driving at right here: your online business can not afford to take cybersecurity flippantly. Particularly, in the event you function in extremely aggressive sectors like manufacturing and provide chain administration. And particularly if your organization has tapped into the Internet of Things software program growth – similar to 72% of your rivals.
From detecting anomalies in tools efficiency earlier than failures happen to monitoring stock ranges in actual time utilizing RFID tags and BLE beacons, there are a lot of thrilling IIoT functions and advantages to contemplate. And simply as some ways your IIoT resolution might compromise your complete IT infrastructure, main to the next penalties:
- Damaged equipment
- Production downtim
- Accidents on the manufacturing unit ground
- Data breach
- Reputational harm
- And direct and oblique monetary losses attributable to all the above
What are the important thing components placing IIoT safety in danger – and the way might your organization foresee and resolve the Industrial Internet of Things safety challenges earlier than catastrophe strikes?
Let’s resolve the riddle collectively!
Rundown of IIoT safety faults and challenges
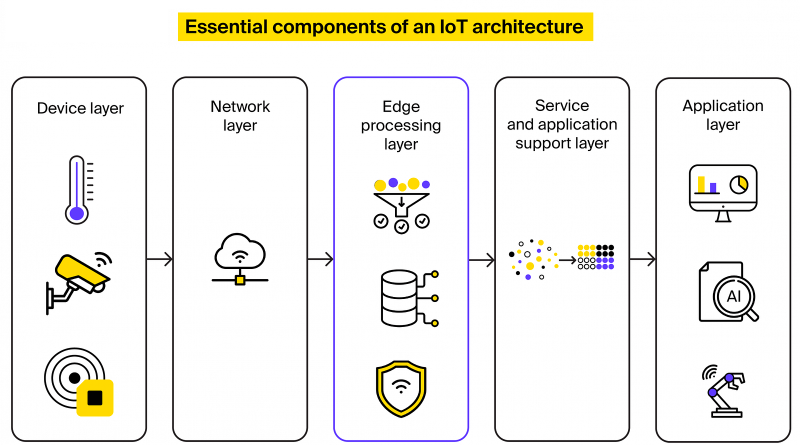
For readability’s sake, let’s outline the Industrial Internet of Things and its expertise elements earlier than zooming in on IIoT safety implications.
The IIoT time period refers to the interconnected community of machines, sensors, controllers, and methods that talk and alternate knowledge with one another and central platforms in industrial settings.
Such cyber-physical methods mix parts of conventional industrial tools with connectivity, knowledge analytics, and knowledge visualization. Companies flip to IIoT consultants to monitor manufacturing and warehouse operations and automate single processes or complete workflows.
Behind the scenes, the Industrial IoT has the identical structure as each different Internet of Things resolution, though edge IoT deployments the place knowledge is analyzed nearer to sensors prevail in industrial settings.
Companies tapping into IIoT might procure brand-new tools enhanced with sensors and supporting connectivity by default or improve current equipment utilizing customized and off-the-shelf IIoT retrofit kits.
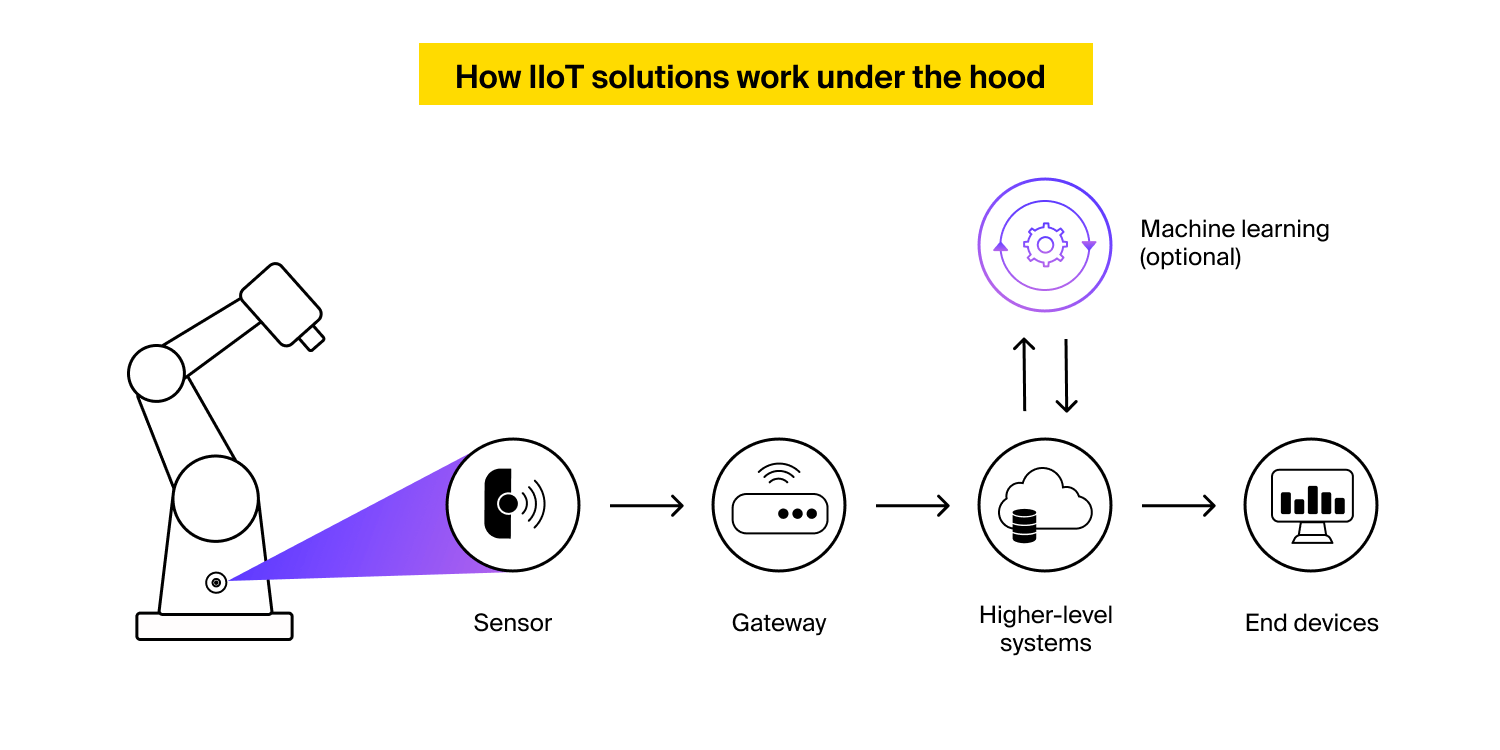
From the Industrial IoT safety standpoint, why is it essential to perceive how IIoT methods operate behind the scenes?
IIoT safety points can manifest themselves at each tier of your cyber-physical system – from programmable controllers to legacy apps containing unpatched vulnerabilities. To mitigate IIoT safety dangers, your organization ought to thus defend all endpoints in your wired or wi-fi community, safe knowledge in transit and at relaxation, and patch safety loopholes in functions comprising your IT infrastructure.
Without additional ado, let’s examine what components undermine safety in IIoT options – and what you are able to do to defend your cyber-physical methods from these threats.
Challenge #1: Unsecured communications
Connectivity applied sciences are the spine of all IoT methods, irrespective of the complexity and space of software.
In industrial settings, as extra units and sensors log on, extra endpoints, communication channels, and knowledge storage options emerge. And this requires a really numerous and, ideally, balanced combination of knowledge and networking protocols assembly particular IIoT safety necessities.
Currently, up to 98% of all IoT site visitors is unencrypted, that means hackers can simply bypass the primary line of protection – e.g., by studying a consumer’s login and password by way of a phishing assault – and lay their fingers in your firm’s knowledge.
Poor encryption practices stem from utilizing legacy communication applied sciences, comparable to Modbus, Profibus, and DeviceWeb. In truth, many of the legacy IIoT communication protocols lack knowledge encryption capabilities altogether, forcing IoT builders to search for workarounds, comparable to implementing VPNs and safe tunnels or gateways and addressing encryption points on the Secure Sockets Layer (SSL)/Transport Layer Security (TLS) degree.
Solution
To safe knowledge alternate between the elements of an IIoT resolution and thus forestall the Industrial Internet of Things safety accidents, we advocate you implement a fail-proof connectivity tech stack consisting of:
- Reliable knowledge protocols. In Industrial IoT, knowledge protocols decide how info is structured, encoded, and interpreted by units. If your organization opts for a wired IIoT deployment, you possibly can facilitate knowledge alternate between related tools and gateways by way of the Ethernet protocols, comparable to Profinet, EtherNet/IP, and Modbus TCP/IP. While these protocols don’t inherently assist knowledge encryption, your IIoT builders can nonetheless make knowledge unreadable to third events by implementing the TLS/SSL tech stack on the transport layer or introducing middleman units, comparable to safe gateways or firewalls, between related units and the community. Should you search for a extra versatile knowledge protocol for IIoT and industrial automation options, we extremely advocate the OPC Unified Architecture (OPC UA) protocol, which helps end-to-end encryption, employs X.509 digital certificates for machine authentication, and can be utilized in each wired and wi-fi IIoT options. When constructing wi-fi IIoT methods, the ITRex workforce often sticks to Message Queuing Telemetry Transport (MQTT), Constrained Application Protocol (CoAP), Advanced Message Queuing Protocol (AMQP), InternetSockets, or RESTful APIs with HTTPS. These trendy protocols provide encryption capabilities by way of TLS/SSL or Datagram Transport Layer Security (DTLS) and assist set up safe communication channels between related tools, gateways, and cloud servers. For extra details about knowledge protocols and their influence on Industrial IoT safety, e book a free session with our R&D workforce.
- Secure networking protocols. Unlike knowledge protocols, which principally cope with info alternate and interoperability, community protocols outline guidelines, requirements, and procedures for a way units are related, how knowledge is transmitted, and the way the elements of an IIoT system work together inside a community. From the Industrial IoT safety standpoint, networking protocols might be engaging targets for hackers. Some causes for that embrace restricted entry management and authentication mechanisms and an absence of knowledge encryption capabilities. Depending in your community structure – i.e., point-to-point, star, or mesh patterns – and meant use circumstances, you possibly can make the most of varied networking protocols to handle IIoT safety challenges. These protocols span Data Distribution Service (DDS), Low Power Wide Area Network (LoRaWAN), Zigbee, WirelessHART, and Narrowband IoT (NB-IoT). To choose the suitable connectivity tech stack assembly your whole IIoT safety wants, it can be crucial to contemplate the kind of cyber-physical system you are wanting to construct, the required knowledge transmission vary, and energy consumption necessities. This might be performed throughout the discovery part of your IoT undertaking.
Challenge #2: Inadequate software program replace practices
Unlike computer systems, tablets, and smartphones, IoT units don’t assist endpoint safety methods, comparable to antivirus applications – just because they usually run extremely custom-made or outdated embedded software program or are particularly designed to be small and energy-efficient.
While you possibly can partially resolve Industrial IoT safety challenges by introducing firewalls, intrusion detection and prevention (IDP), and machine management mechanisms on the community degree, upgrading the functions constituting your IIoT software program ecosystem to the newest model turns into important for resolving attainable IIoT safety points.
Speaking of IIoT software program, we’d like to draw the road between embedded methods, comparable to firmware, middleware, and working methods (OSs), and unusual software program – assume net, desktop, and cell functions facilitating machine administration.
Due to IIoT machine design constraints and a lot of endpoints inside a cyber-physical system, patching IIoT software program safety vulnerabilities is a job few industrial corporations can handle. That’s why up to 65% of producers nonetheless use outdated working methods ridden with zero-day safety vulnerabilities.
Solution
To mitigate IIoT cybersecurity dangers, an industrial firm will need to have an environment friendly software program replace administration mechanism in place.
Here at ITRex, we’re robust advocates of software program and firmware updates over the air (OTA). In this situation, a cloud-based platform powered by AWS IoT Device Management, Azure IoT Hub, or pre-configured SaaS options like Bosch IoT Rollouts mechanically delivers software program updates to edge units, controllers, and gateways.
A correctly configured machine administration platform may also maintain higher observe of your machine fleet, optimize replace rollouts contemplating device-specific settings and safety necessities, and notify your IT workforce in emergencies.
Challenge #3: Poor bodily safety measures
Network IIoT safety apart, a cyber-aware industrial firm must also forestall cybercriminals and malicious insiders from stealing {hardware} with the aim of scanning the units’ inside and infesting them with viruses and spying applications.
Insufficient bodily safety measures not solely compromise the integrity and confidentiality of delicate knowledge, but in addition lead to service disruptions, operational downtime, and monetary losses. The repercussions of bodily safety vulnerabilities can prolong past the rapid influence, doubtlessly endangering public security and demanding infrastructure.
Solution
To handle the poor bodily safety points in industrial IoT, a multi-faceted method is required. Here’s what your organization ought to do as a part of the bodily IIoT safety overhaul:
- Prioritize the implementation of strong entry management mechanisms. This consists of measures comparable to role-based entry management (RBAC) to related tools, biometric authentication, pc imaginative and prescient-powered video surveillance, and the implementation of intrusion detection methods
- Conduct common bodily safety audits and threat assessments. The Industrial Internet of Things safety audits assist determine vulnerabilities early on and develop applicable mitigation methods. This proactive method allows organizations to keep one step forward of potential threats and take preventive measures to safeguard their IIoT methods. In apply, this implies disconnecting units with proof of tampering from the community, hiding producer markings on the units, and, when attainable, eradicating pointless IIoT resolution elements to forestall reverse engineering occasions
- Implement complete worker coaching applications. Raising consciousness about bodily safety dangers and finest practices is essential to fortifying the Industrial Internet of Things cybersecurity (extra on that later). Collaboration between IT and bodily safety groups can be very important. This partnership ensures a holistic method to safety, the place each digital and bodily points are thought of and synchronized to present sturdy safety towards rising IIoT safety threats.
Challenge #4: Limited visibility into machine and community exercise
Up to 90% of organizations report having shadow IoT units on their community, with 44% of the respondents admitting these units had been related with out the data of their safety or IT groups.
As a end result, corporations are unaware of which units talk with one another, what info they collect and alternate, and whether or not this info is inaccessible to third events.
And the truth that IIoT safety audits stretch far past figuring out {hardware} options by their IP and working system solely complicates the matter.
Solution
There are a number of steps you possibly can take to obtain machine and community visibility in IIoT deployments:
- Analyze all community communications utilizing deep packet inspection (DPI) options
- Collect exhaustive machine info, together with {hardware} sort, mannequin, serial quantity, and embedded system variations
- Group your units based mostly on their sort, operate, mission criticality, and potential IIoT safety dangers
- Create digital native space networks (VLANs) for each machine group to improve site visitors visibility and management
- Make use of dependable machine administration platforms, comparable to AWS IoT Core, Azure IoT Hub, and PTC ThingWorks, to enhance machine inventories, monitoring, configuration, replace rollouts, and troubleshooting
Challenge #5: Insufficient worker coaching and cyber-awareness
As we have talked about earlier, an absence of collaboration and coordination between info expertise (IT) and operational expertise (OT) groups can lead to poor IIoT safety administration practices.
While tools operators and manufacturing unit managers correctly take care of related machines, they know little in regards to the embedded and connectivity applied sciences that energy them. IT groups, quite the opposite, are well-versed in conventional info safety however have a tendency to deal with IIoT options like unusual {hardware}.
This might lead to low patch ranges, restricted visibility into community exercise, and misconfigurations of the Industrial Internet of Things methods. Additionally, cybercriminals might exploit your worker’s restricted data of IIoT safety finest practices by way of phishing assaults and impersonation. Your workforce may select weak passwords or reuse passwords throughout functions, which can open a backdoor to your IT infrastructure, undermining IIoT software program safety.
Solution
Here’s a high-level plan that would assist your organization increase cybersecurity consciousness amongst workers:
- Create coaching applications particularly tailor-made to the Industrial IoT setting. These applications ought to cowl subjects comparable to cybersecurity fundamentals, IoT machine safety, safe configuration practices, password hygiene, recognizing and reporting potential safety incidents, and compliance with inside safety insurance policies and procedures.
- Conduct common coaching classes to guarantee workers keep up-to-date with the newest cybersecurity threats and finest practices. This might be performed by way of workshops, seminars, webinars, or on-line coaching modules in your studying administration system (LMS). As a part of the coaching actions, for example, you possibly can educate your workers to acknowledge and reply to IIoT safety threats by way of phishing simulations and penetration testing. You must also tailor coaching applications to particular job features, making certain that workers obtain the coaching related to their tasks. For instance, IT workers might require extra technical coaching, whereas operational workers might have coaching on safe machine utilization and bodily safety.
- Develop complete insurance policies and procedures that handle the distinctive Industrial Internet of Things safety challenges. Communicate these insurance policies successfully to workers and guarantee they perceive their roles and tasks in sustaining safety. Regularly evaluate and replace these insurance policies as expertise and threats evolve.
- Promote a tradition of IIoT safety consciousness and accountability all through the group. Encourage workers to report any safety incidents or suspicious actions promptly. Emphasize that cybersecurity is everybody’s duty, from high administration to frontline workers, and reward workers for demonstrating good safety practices.
- Consider partnering with exterior Industrial IoT consultants or consultants to conduct safety assessments. External consultants can deliver useful insights, trade finest practices, and the newest risk intelligence to improve worker coaching applications. Additionally, they may allow you to deliver the so-called “safety by design” practices into the IIoT software program growth course of and elicit useful and non-functional necessities for IIoT deployments.
On a remaining be aware
IIoT adoption charges have soared in recent times – and so have the high-profile assaults focusing on important IIoT infrastructures within the industrial phase.
According to a latest survey from Check Point, within the first two months of 2023, 54% of corporations suffered IoT-related assaults, with an estimated 60 assaults per week per group (41% up from final 12 months). Among the units most inclined to hacker assaults had been routers, community video recorders, and IP cameras – briefly, {hardware} that includes the spine of each firm’s IT infrastructure.
Even in case your IT workforce follows IIoT safety finest practices all through the event and implementation course of, there is no assure hackers will not train management over your tools and knowledge by exploiting vulnerabilities in apps and units outdoors the IIoT ecosystem. That’s why your organization wants an all-embracing safety technique – and here is what ITRex can do for you!
Whether you are contemplating launching an IIoT pilot or need assistance scaling an Industrial IoT proof of idea (PoC) throughout different use circumstances, drop us a line! We’re well-versed in enterprise evaluation, embedded system engineering, cloud computing and DevOps, and end-user software growth.
The publish IIoT Security Challenges & Tips to Navigate Them appeared first on Datafloq.